Log4J Vulnerability
Recently vulnerabilities for the Java module Log4J have been disclosed, and a lot of applications use this module in their logging. Please refer to the below URL for more details:
Reference Articles
https://sysdig.com/blog/exploit-detect-mitigate-log4j-cve/
All versions of Log4J below 2.17.0 are affected.

Recommended Action
We’ve written a script to detect any installations of Log4J and their versions. We recommend running the scan on all machines in your environment over the next few days effective in the next hour.
It may take a little longer given PC\HDD performance etc.
Procedure name: "Log4J Vulnerability Scan and Report [CF, GetFile]" - It's looking for any .jar file with log4j* on the C: drive. It will be updating the custom field.
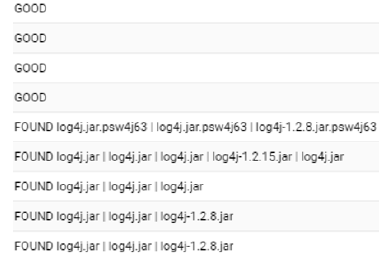
If nothing is found it will update the custom field with the status "GOOD". If it finds something it will update "FOUND" with a pipe-separated list of the files and versions. It will also create a detailed .csv report of the full paths and copies it up to the agent's GetFiles folder for further investigation.
If the script is blocked by AV it will update "Log Missing" in the CF.
The script, log, data, and report are located on each machine at our standard logging location.
We’ve got another script "Collate Log4J Results to GetFile [On-Prem, Params]" that collates this data into a single report.
Known Issues
Unfortunately, the updating and mitigation cannot be scripted as it’s per-app. Our other customers are taking these applications offline or removing them.



