Spring4Shell Vulnerability
Recently vulnerability named "Spring4Shell Vulnerability" is for apache servers, the behavior of the vulnerability is very generic, however, there may be other ways to exploit it.
These are the prerequisites for the exploit:
- JDK 9 or higher
- Apache Tomcat as the Servlet container
- Packaged as WAR
- spring-webmvc or spring-webflux dependency
Please refer to the below URL for more details:
Reference Articles
https://github.com/tweedge/springcore-0day-en
https://tanzu.vmware.com/security/cve-2022-22965

Recommended Action
There are updates out to mitigate this for both VMWare and the spring framework so machines that are up to date and vendors using the spring framework are updated should not be affected. We would recommend updating these applications to the latest versions.
We’ve written a script to detect the active apache and java ports running against localhost. We recommend running the scan on all machines in your environment over the next few days starting effectively in the next hour.
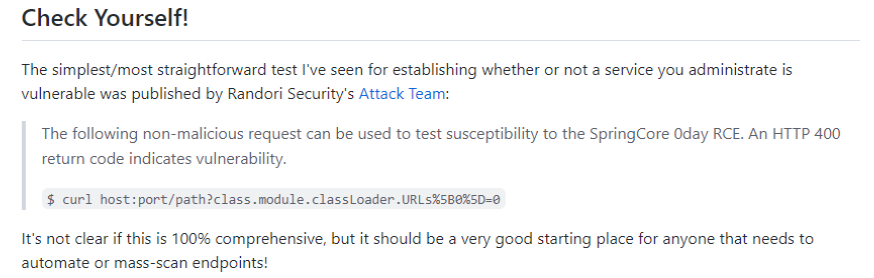
Procedure name: "Spring 4 Shell Apache Check" - It will be updating the custom field.
If nothing is found it will update the custom field with the status "Machine Safe". If it finds something it will update "Machine is theoretically vulnerable" as the documents suggest that it may not be comprehensive.
If the script is blocked by AV it will update "Log Missing" in the CF.
Known Issues
Unfortunately, the updating and mitigation cannot be scripted as it’s per-app. Our other customers are taking these applications offline or removing them.



